Dangers of Cell Tower Spoofers, AKA IMSI Catchers
Cell tower spoofers, also known as International Mobile Subscriber Identity (IMSI) catchers, are clandestine surveillance devices used to intercept and monitor mobile communications. While originally developed for law enforcement and intelligence agencies, these devices have increasingly fallen into the hands of malicious actors, posing serious dangers to privacy and security. Understanding the risks associated with cell tower spoofers is essential for individuals and organizations seeking to protect their sensitive information and communications.
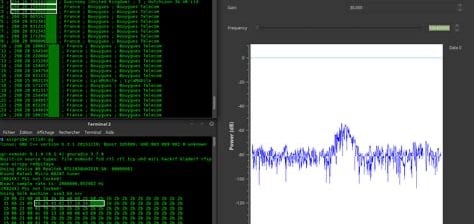
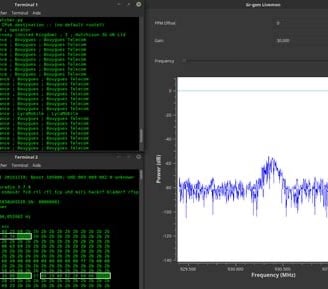
Cell tower spoofers, also known as International Mobile Subscriber Identity (IMSI) catchers, are clandestine surveillance devices used to intercept and monitor mobile communications. While originally developed for law enforcement and intelligence agencies, these devices have increasingly fallen into the hands of malicious actors, posing serious dangers to privacy and security. Understanding the risks associated with cell tower spoofers is essential for individuals and organizations seeking to protect their sensitive information and communications.
Cell tower spoofers operate by mimicking legitimate cell towers, tricking nearby mobile devices into connecting to them instead of genuine network towers. Once connected, the IMSI catcher can intercept and monitor all communications transmitted between the mobile device and the cellular network, including voice calls, text messages, and data transmissions. This interception capability allows attackers to eavesdrop on sensitive conversations, steal personal information, and track the movements of individuals without their knowledge or consent.
One of the most significant dangers of cell tower spoofers is the potential for unauthorized surveillance and invasion of privacy. By intercepting and monitoring mobile communications, attackers can gain access to a wealth of sensitive information, including personal conversations, financial transactions, and location data. This information can be exploited for various nefarious purposes, including identity theft, extortion, and blackmail, posing serious risks to individuals' privacy and security.
Moreover, cell tower spoofers can be used to conduct targeted attacks against individuals or organizations. By intercepting communications and gathering intelligence, attackers can identify potential targets for further exploitation, such as high-profile individuals, government officials, or corporate executives. This targeted surveillance can enable attackers to gather sensitive information, gather leverage for blackmail or extortion, or even orchestrate physical attacks or acts of sabotage.
Furthermore, cell tower spoofers can be used to conduct large-scale surveillance operations, monitoring communications across entire neighborhoods, cities, or regions. This mass surveillance capability poses significant risks to civil liberties and democratic values, undermining trust in institutions and eroding individuals' rights to privacy and freedom of expression. Moreover, the indiscriminate collection of data can lead to the unjust targeting of innocent individuals and the chilling effect on free speech and dissent.
To mitigate the dangers of cell tower spoofers, individuals and organizations can take several proactive measures to protect themselves against surveillance and interception. First and foremost, individuals should be vigilant about their surroundings and watch for signs of suspicious activity, such as unexplained drops in signal strength or unexpected changes in network behavior. Additionally, individuals can use encryption and secure communication protocols to protect their sensitive information from interception and monitoring by attackers.
In conclusion, cell tower spoofers, also known as IMSI catchers, pose serious dangers to privacy and security by intercepting and monitoring mobile communications. Understanding the risks associated with these devices is essential for individuals and organizations seeking to protect their sensitive information and communications from unauthorized surveillance and interception. By remaining vigilant, using encryption and secure communication protocols, and employing specialized countermeasures, individuals and organizations can mitigate the dangers posed by cell tower spoofers and safeguard their privacy and security in an increasingly interconnected world.
